Sign Windows EXE File with Code Signing Certificate
In this article, we will explore the process of signing Windows EXE files using a code signing certificate.
- Download and install the Exe and Dll File Repair Tool.
- The software will scan your system to identify issues with exe and dll files.
- The tool will then fix the identified issues, ensuring your system runs smoothly.
Is it safe to sign exe with certificate?
When it comes to signing exe files with a certificate, it is safe and highly recommended. A code signing certificate, such as an Extended Validation Certificate, provides authentication and ensures the integrity of the software. By signing the exe file, you are adding a digital signature that verifies the source and integrity of the code. This helps users trust the software and protects against tampering or malware. Additionally, signed exe files are less likely to trigger warnings from antivirus software, making it easier for users to download and install your software.
To sign an exe file, you can use tools like the Microsoft Windows SDK or third-party providers like Comodo Cybersecurity or Gen Digital. Keep in mind that there may be fees associated with obtaining a code signing certificate. So, if you want to enhance the security and trustworthiness of your software, signing your exe file with a certificate is a safe and valuable step to take.
Origin and Usage of signed exe with certificate
A signed EXE file with a certificate is a way to verify the authenticity and integrity of a Windows executable file. It provides assurance that the file has not been tampered with and comes from a trusted source. The certificate used for signing is issued by a trusted certificate authority, such as Comodo Cybersecurity or Gen Digital, and can be obtained through a process called code signing.
To sign a Windows EXE file, you will need a code signing certificate, which can be acquired through various vendors. This certificate ensures that your file is trusted by Windows operating systems and antivirus software.
By signing your EXE file, you add an extra layer of security and protect users from potential malware or unauthorized modifications. It also allows your software to comply with Windows 10 security requirements and avoid any warning messages that may deter users from downloading or running your program.
To sign an EXE file, you will typically need to use a software development kit (SDK) provided by Microsoft, such as the Microsoft Windows SDK. This SDK includes tools and instructions on how to sign your files using Transport Layer Security (TLS) protocols and SHA-2 hashing algorithms.
Signing an EXE file with a certificate does come with a cost, as certificate authorities charge a fee for issuing and maintaining the certificate. Additionally, there may be value-added tax (VAT) or other charges depending on your jurisdiction.
Once your EXE file is signed, users can verify its authenticity by checking the certificate details. This can be done by right-clicking the file, selecting “Properties,” and navigating to the “Digital Signatures” tab. Here, they can view the certificate information and confirm that it was issued by a trusted authority.
Malware associated with signed exe with certificate
When signing a Windows EXE file with a code signing certificate, it’s important to be cautious of malware associated with signed executables. Malicious actors can use this method to deceive users and infect their systems.
To protect yourself, always verify the source of the signed executable before running it. Look for trusted publishers and ensure that the certificate used is valid, such as an Extended Validation Certificate.
Additionally, be cautious of any suspicious behavior or unexpected requests during the installation process. Avoid clicking on suspicious links or downloading files from untrusted sources.
If you encounter any issues or suspect malware, reach out to technical support or consult with a professional to ensure your system’s security.
Troubleshooting: Can’t delete signed exe with certificate
If you’re having trouble deleting a signed .exe file with a certificate, follow these troubleshooting steps:
1. Check that you have administrative privileges on your Windows 10 system.
2. Make sure the file is not currently running or being used by any other program.
3. Try restarting your computer and then deleting the file.
4. If the file is located on a USB flash drive, ensure that the drive is not write-protected.
5. If you’re still unable to delete the file, try using the Command Prompt to force delete it. Open Command Prompt as an administrator and use the del command followed by the file path and name.
6. If all else fails, contact technical support for further assistance.
High CPU usage caused by signed exe with certificate
When signing a Windows EXE file with a code signing certificate, it’s important to be aware that it may result in high CPU usage. This can be caused by the process of signing the file, which requires significant computational resources. To mitigate this issue, there are a few things you can do. First, make sure you have a strong and reliable internet connection to ensure smooth communication with the certificate authority.
Additionally, consider using a more powerful computer or increasing the available resources, such as RAM, to handle the signing process more efficiently. You can also try using a software development kit (SDK) specifically designed for code signing to streamline the process.
Sign exe with certificate as a system file
To sign a Windows .exe file with a code signing certificate, follow these steps:
1. Open the Command Prompt as an administrator.
2. Navigate to the directory where the .exe file is located using the “cd” command.
3. Use the “signtool” command to sign the file: signtool sign /fd sha256 /tr http://timestamp.digicert.com /td sha256 /f “path\to\certificate.pfx” /p “certificate_password” “file.exe”.
4. Replace “path\to\certificate.pfx” with the path to your code signing certificate, and “certificate_password” with the password for the certificate.
5. Press Enter to execute the command.
6. Once the signing process is complete, the .exe file will be signed with the code signing certificate.
By signing the .exe file, you can ensure its authenticity and integrity, providing users with confidence in its source. This is especially important for software distribution and preventing tampering or unauthorized modifications.
Associated software and creator of signed exe with certificate
- Code Signing Certificate: A digital certificate used to sign Windows EXE files, confirming the authenticity and integrity of the software.
- Microsoft SignTool: A command-line tool provided by Microsoft to digitally sign code, including Windows EXE files, using a code signing certificate.
- Windows SDK (Software Development Kit): A collection of software tools and libraries provided by Microsoft to developers for building Windows applications.
- Microsoft Visual Studio: An integrated development environment (IDE) provided by Microsoft, which includes tools for code signing and certificate management.
- Windows Certificate Store: A repository in Windows operating systems that stores digital certificates, including code signing certificates.
- Timestamping Authority: A trusted third-party service that provides timestamp information to digitally signed code, ensuring the validity of the signature even after the certificate expires.
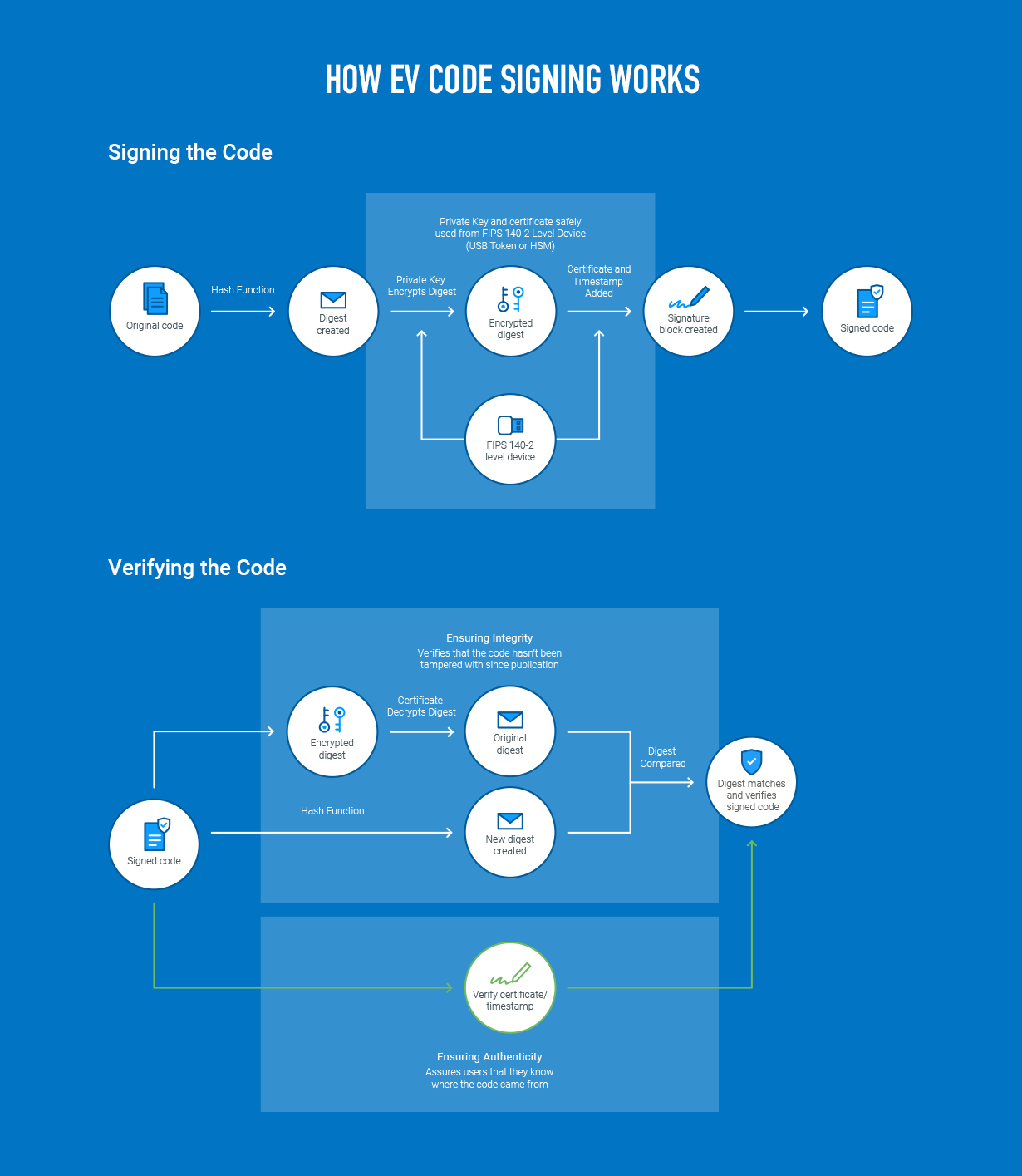
- Windows Defender SmartScreen: A security feature in Windows that warns users when they attempt to run unrecognized or potentially malicious software, including unsigned EXE files.
- Microsoft Authenticode: A digital signature technology developed by Microsoft for verifying the authenticity and integrity of Windows software.
- Code Signing Hardware Token: A physical device used to securely store code signing certificates and private keys, providing an extra layer of protection against unauthorized access.
Is it safe to end task for signed exe with certificate?
When it comes to ending a task for a signed EXE file with a certificate, it is generally safe to do so. The certificate serves as a verification of the file’s authenticity and integrity. However, it is important to exercise caution and ensure that the EXE file is indeed signed with a valid code signing certificate.
To end the task for a signed EXE file, you can follow these steps:
1. Open the Task Manager by pressing “Ctrl + Shift + Esc” or right-clicking the taskbar and selecting “Task Manager”.
2. In the Task Manager, go to the “Processes” tab.
3. Look for the EXE file in the list of processes. You can sort the list alphabetically or use the search function to find it.
4. Right-click on the EXE file and select “End Task” or “End Process”.
5. Confirm the action if prompted.
Latest Update: July 2025
We strongly recommend using this tool to resolve issues with your exe and dll files. This software not only identifies and fixes common exe and dll file errors but also protects your system from potential file corruption, malware attacks, and hardware failures. It optimizes your device for peak performance and prevents future issues:
- Download and Install the Exe and Dll File Repair Tool (Compatible with Windows 11/10, 8, 7, XP, Vista).
- Click Start Scan to identify the issues with exe and dll files.
- Click Repair All to fix all identified issues.
Description of the sign exe with certificate process
When signing a Windows EXE file with a code signing certificate, the process involves several steps. First, generate a public key certificate for your application. This certificate will be used to verify the authenticity of your EXE file. Next, ensure that your certificate is issued by a trusted Certificate Authority (CA) to prevent security warnings.
To sign your EXE file, open the SignTool. exe utility, which is included in the Windows SDK. Use the command “signtool sign /f [your certificate file] /p [your certificate password] [your EXE file]” to sign the file with your certificate.
Signed exe with certificate not responding
When signing a Windows EXE file with a code signing certificate, you may encounter issues if the signed EXE is not responding. This can be frustrating, but there are a few steps you can take to troubleshoot the problem.
First, check that the certificate used for signing the EXE is valid and has not expired. Sometimes, an expired certificate can cause the EXE to stop responding.
Next, ensure that the certificate is installed correctly on the machine where the EXE is being run. If the certificate is missing or not properly installed, it can lead to non-responsiveness.
Additionally, check if the EXE file itself is corrupted or damaged. If it is, signing it with a certificate won’t fix the issue.
Finally, make sure that the EXE file is compatible with the operating system it is being run on. Compatibility issues can also cause non-responsiveness.
Removal tools for signed exe with certificate
- Step 1: Download and install a reputable removal tool
- Go to a trusted website that offers removal tools for signed exe with certificates
- Search for a removal tool that specifically targets signed exe files with certificates
- Download the removal tool and save it to a location on your computer
- Double-click on the downloaded file to start the installation process
- Follow the on-screen instructions to complete the installation
- Step 2: Launch the removal tool
- Locate the removal tool on your computer
- Double-click on the shortcut or executable file to launch the removal tool
- Wait for the removal tool to initialize and prepare for the removal process
- Step 3: Scan your computer for signed exe files with certificates
- Click on the “Scan” button or similar option within the removal tool
- Allow the removal tool to scan your computer for any signed exe files with certificates
- Wait for the scan to complete, as it may take some time depending on the size of your computer and the number of files to be scanned
- Step 4: Review the scan results
- Once the scan is finished, the removal tool will display a list of signed exe files with certificates found on your computer
- Review the scan results carefully to identify any potentially malicious or unwanted files
- Pay attention to the file names, paths, and other details provided by the removal tool
- Step 5: Select and remove the signed exe files with certificates
- Check the box next to each signed exe file with a certificate that you want to remove
- Click on the “Remove” or similar button within the removal tool
- Confirm your action when prompted by the removal tool
- Wait for the removal tool to delete the selected signed exe files with certificates from your computer
- Step 6: Restart your computer
- Once the removal process is complete, it is recommended to restart your computer
- Restarting will ensure that any remaining traces of the signed exe files with certificates are removed from memory and system processes
- After the restart, your computer should be free from the signed exe files with certificates that you have removed
Startup impact of signed exe with certificate
When you sign a Windows EXE file with a code signing certificate, it can have a significant impact on your startup. First and foremost, it enhances the security and trustworthiness of your software. Users can verify that the EXE file hasn’t been tampered with and comes from a trusted source. This can boost user confidence and increase adoption rates. Additionally, signed EXE files are less likely to be flagged by antivirus software as potentially harmful, reducing the risk of false positives.
This can save you time and effort in resolving false alarms. Another advantage is that signed EXE files can bypass certain security measures, such as SmartScreen filters, making it easier for users to install your software.
Performance impact of signed exe with certificate
The performance impact of signing a Windows EXE file with a code signing certificate is minimal. When a file is signed with a certificate, it adds a digital signature to the executable, ensuring its authenticity and integrity. This process involves generating a cryptographic hash of the file and encrypting it with the private key of the certificate.
Verifying the digital signature during execution does have a small impact on performance, but it is negligible for most applications. It adds a few milliseconds to the startup time, but once the file is loaded, there is no noticeable difference in performance.
It’s important to note that the performance impact may vary depending on the size and complexity of the executable. However, for typical software applications, the impact is insignificant.
Update and download options for signed exe with certificate
Sign Windows EXE File with Code Signing Certificate
Here are the update and download options for signed exe with a code signing certificate:
| Option | Description |
|---|---|
| Option 1 | This option allows you to sign your Windows EXE file using a code signing certificate. It ensures that the file comes from a trusted source. |
| Option 2 | With this option, you can download the signed EXE file from a trusted website. Make sure to verify the certificate details before proceeding with the download. |
| Option 3 | Another option is to update your existing EXE file by applying the code signing certificate. This ensures that the file remains secure and trusted by users. |
Compatibility with different Windows versions
To ensure compatibility, it is important to use a code signing certificate that is compatible with the Windows operating system versions you intend to target. This will help ensure that users can install and run your signed EXE file on their respective Windows versions without encountering compatibility issues.
When choosing a code signing certificate, look for options that support a wide range of Windows versions, including older ones. This will ensure that your signed EXE file can be installed and trusted by users running different versions of Windows.
Additionally, it is recommended to use a code signing certificate that adheres to industry-standard hashing algorithms, such as SHA-2, to maximize compatibility and security.
By selecting a compatible code signing certificate, you can ensure that your EXE file is trusted and can be installed on different Windows versions, providing a seamless experience for users.
Alternatives to signing exe with certificate
- Timestamping: Utilize a timestamp server to add a timestamp to the signed code, extending its validity beyond the expiration date of the certificate.
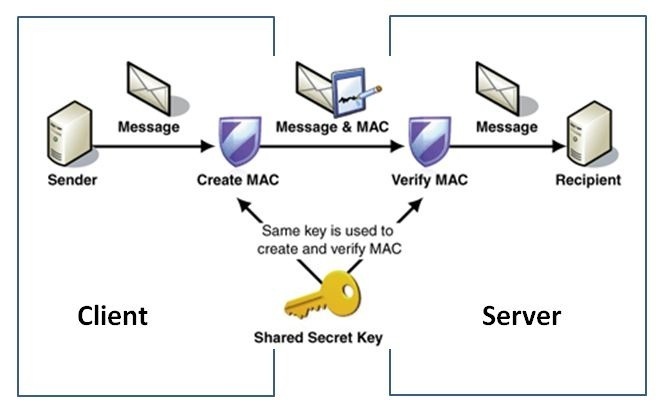
- Hash-based Message Authentication Code (HMAC): Employ HMAC to verify the integrity and authenticity of the file without the need for a digital certificate.
- Applocker: Leverage Windows Applocker to create rules that restrict which applications can run on a system, reducing the reliance on code signing certificates.
- Windows Defender SmartScreen: Utilize Windows Defender SmartScreen reputation-based system to build trust with users, even without code signing.
- Code Integrity Policy: Implement Code Integrity Policies to ensure that only trusted applications can be executed on a system, mitigating the need for code signing certificates.
- Signed PowerShell Scripts: Sign PowerShell scripts using a self-signed certificate or a certificate from an internal certificate authority (CA) to establish trust.
- Containerization: Encapsulate applications within containers to isolate and protect them, reducing the need for code signing certificates.
- Application Whitelisting: Employ application whitelisting techniques to allow only approved applications to run, eliminating the dependency on code signing certificates.
- Secure Code Development: Follow secure coding practices to minimize the risk of malicious code injection, reducing the need for code signing certificates.


